Digitale Gesellschaft
A non-profit organisation that provides information and advice on consumer and legal issues in the digital space, assesses technology impacts with regard to possible effects on basic and human rights and offers services, software projects and workshops on "digital self-defense".
Digitale Gesellschaft fights for our rights of freedom in a networked world.
Contents
Introduction
Part 1: Surfing with little trace
Part 2: Surfing anonymously
Summary
Introduction
Where is the danger?
Where do we leave traces?
Who are the actors?
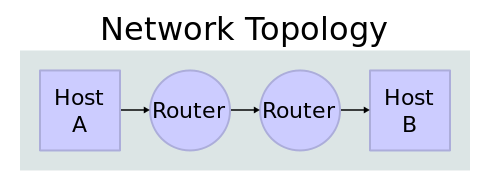
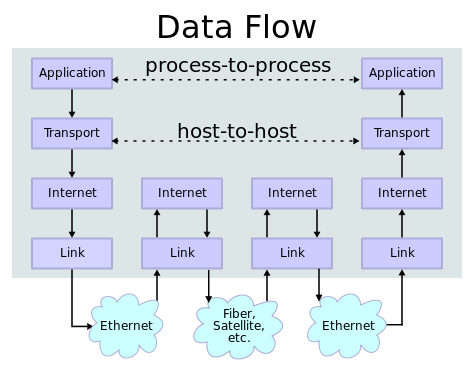
Internet & World Wide Web
We leave diverse traces
At the visited Webservers
and on all other servers from which content is downloaded on behalf of a page visited
During data transfer
Locally on the Computer/Smartphone
Who are the actors?
Server operators
Server's log files analysis
Possibly through Google Analytics
Example:
The example of the newspaper NZZ demonstrates that accesses to a certain page from within NZZ campus can be traced both by evaluating the server logs and by (potentially payable) queries to Google Analytics.
Who are the actors?
Trackers
Advertisement networks, Google, Facebook & Co.
Traceability & identification
Profile building
Who are the actors?
State surveillance
Within criminal cases
"Prevention" through intelligence services
Data retention & tapping fiber-optic communications
Source: Wikipedia
If necessary, prepare a demo with different strict settings and blocker extensions.
Part 1: Surfing with little trace
Browser traces
Browser settings
Trackers
Search engines
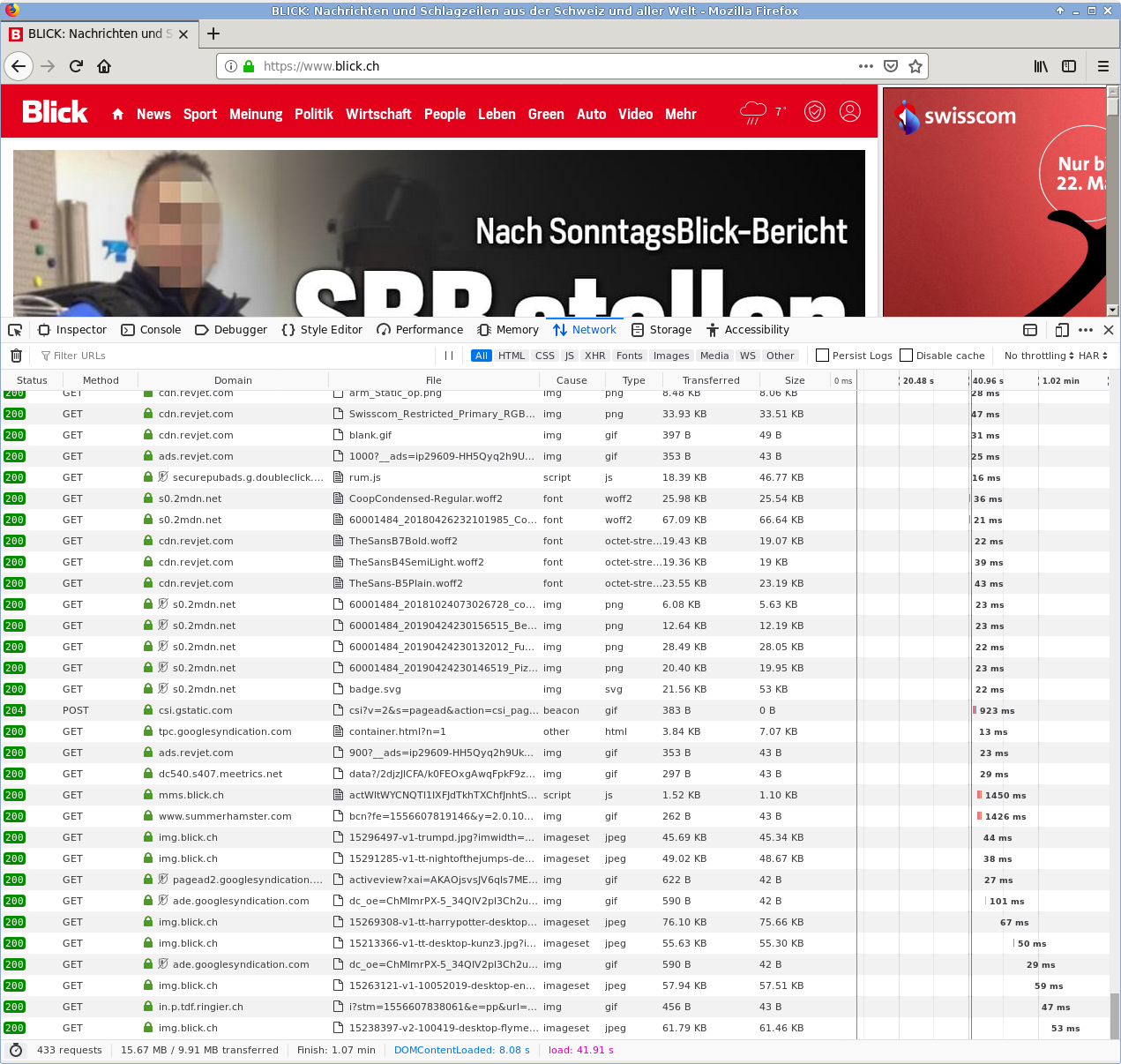
Traces: Webserver Logs
URL: www.digitale-gesellschaft.ch/uber-uns
IP-Address: 80.215.220.52
Browser: Firefox/104.0
Operating System: Ubuntu Linux x86_64
Referrer: www.digitale-gesellschaft.ch/aktiv-werden
Date: 19.07.2022 14:32:01
URL: The resource (page) accessedIP-Address: The connection called upBrowser: The make and version of the browserOperating System: Operating system make and CPU architectureReferrer: Origin page (from which previous page the URL was called up)Date: Time of creation of the HTTP message with these contents
Traces: Webserver
Cookies and also Device- and User Fingerprinting
Info about extensions, fonts, screen resolutionMetadata
Data content (e.g. Basket, Settings, ...)
Browser traces: data transfer
Routers, Firewalls, Proxies(*)
Tapping copper and fiber-optic communications (Kabelaufklärung)
Connection data
Data content
Federal Intelligence Service
But also NSA, GCHQ, BND, etc.
(*) Proxy: Special case, as usage log data is created "inside", but the individual usage is concealed from the outside.
Datenspur einer Übertragung
Browser traces: Data retention
Traces: Local Device
Local Computer
Web-Storage (local or session), Cookies, etc.
Cache memory
Browser history
Smart Device
Traces: Remedy
Server: block trackers, delete cookies, clear "local web storage"
Data transfer: Attention to encryption (https , 🔒)
and do not use mobile phones Local: Delete regularly Cache and Browser history
Depending on the time, provide a demo and questions here if necessary.
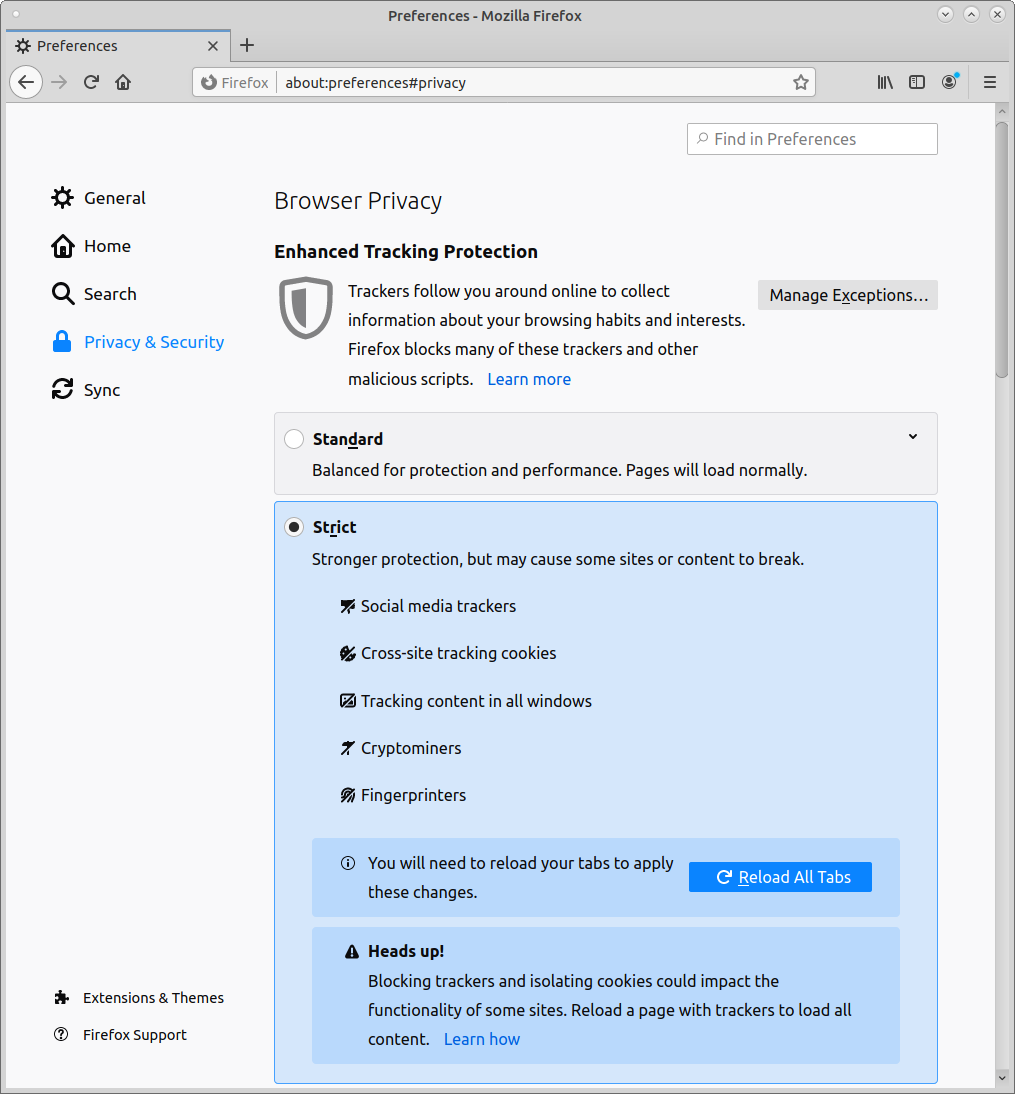
Browser settings
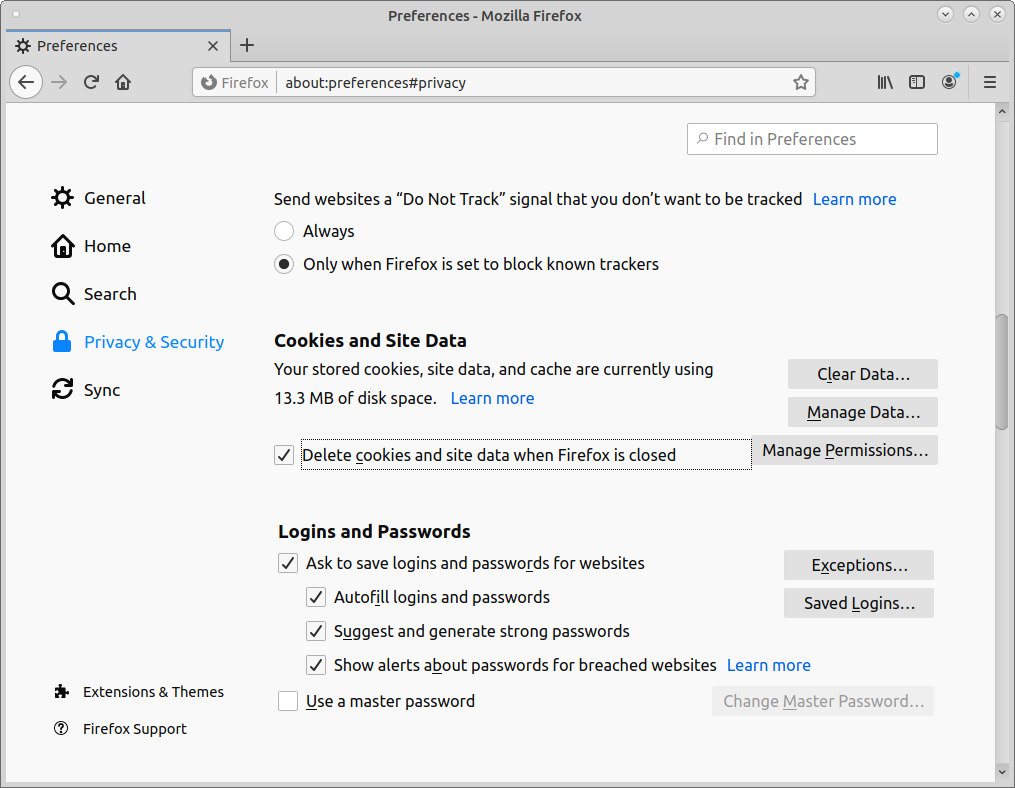
Under "Privacy & Security"
Change Enhanced Tracking Protection
Browser settings: History
Also under "Privacy & Security"
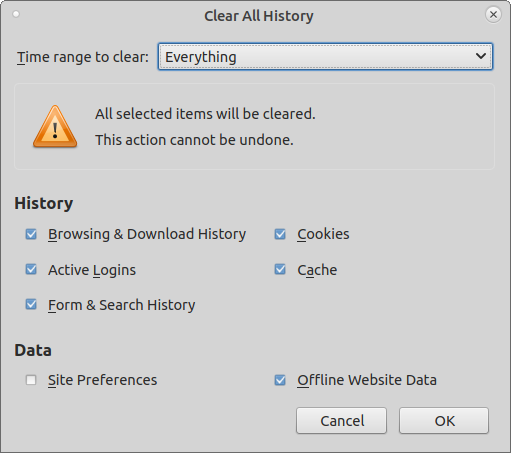
Select "Delete cookies and site data when Firefox is closed"
Manually with key shortcut Ctrl-Shift-Delete
Delete everything, including Offline Website Data
Part 2: Surfing anonymously
Overview
Software installation
Tor Browser
Onion Services
Tor Server
Anonymity on the net
Use of proxies
Operator must not be able to lift anonymity
All communication layers must be considered
network connection layer
application layer
DNS (domain name services) for resolving hostnames into ip network addresses
Tor Project: Purpose
Tor provides anonymous, secure and censorship-resistant communication (connections)
Hides IP addresses from Client and eventually Server
Tor Browser hardens Browser and eliminates distinguishing features
Cookies and IDs, Fingerprinting
Separation of software development and operation
Tor Project: Overview
Opensource project
Very well documentated and extensively studied
Non-profit Organisation, ~20 employees (2020)
Financed through donations
approx. 2-3 billion users
approx. 6'500 relays, exit traffic volume:
~650 GBit/s advertised
~250 Gbit/s consumed
Tor servers of the Digital Society
Metrics: https://metrics.torproject.org/bubbles.html
Tor Browser installation
Ready to use package with
Tor (Client)
Advanced and customized Firefox
Download from Project website
If possible, do not make adjustments or install extensions
Onion Services
Also known as «Hidden Services»
Connecting Tor network with Web servers
Both communication partners are "unknown"
Communication through Rendezvous points
Self-authentication
End-to-End encryption
Example
Whistleblower portal (SecureDrop, GlobaLeaks)
Senders are forced to use Tor and protect themselves
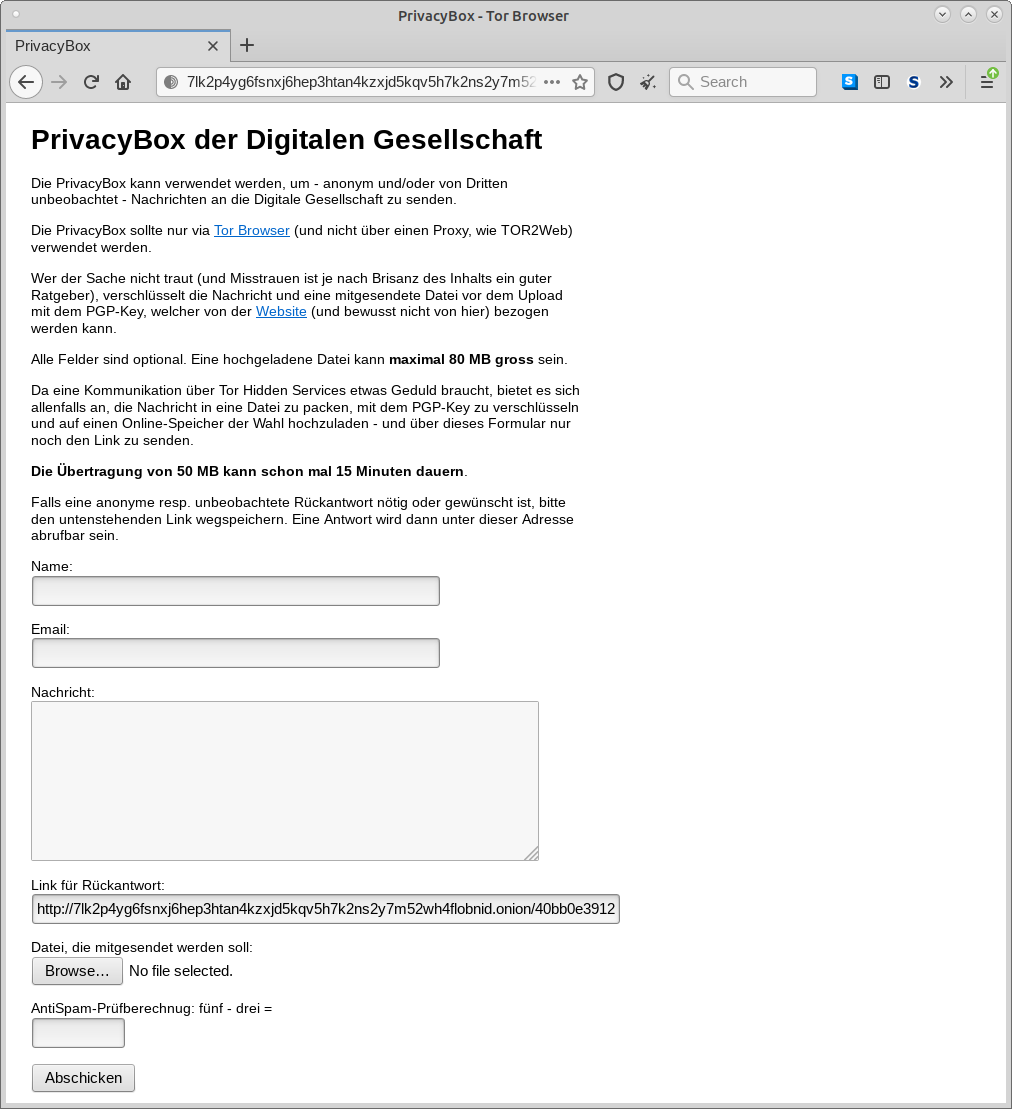
PrivacyBox by Digitale Gesellschaft
The Tor-Server of Digitale Gesellschaft
4 Servers in Switzerland
Total 13 Exit-Node instances (2.5 Gbit/s)
One of the biggest Exit-Node operators
The network is maintained with donations
Summary
The most important tips for secure surfing
The most important tips for secure surfing
Low trace surfing for daily use
Delete often Cookies (and History/Cache)
Block trackers and thus Cookies
Choose privacy friendly search engines
Do not use a mobile phone
The most important tips for secure surfing
Anonymous surfing
for research purposes
As a Whistleblower/Informant
Use the Tor Browser from Torproject.org
related links
The dossiers of the Digiges Tracking & Profiling Expert Group also contain many further links
Digitale Gesellschaft